Cyber Talk-2 From VPN Killer to Zero Trust Platform: The Zscaler Evolution
Zscaler, a pioneer in Zero Trust and cloud-native security
From VPN Killer to Zero Trust Platform: The Zscaler Evolution
On 5/27/2025, Cloud security provider Zscaler has agreed to acquire software company Red Canary for an undisclosed sum. The deal will see Zscaler create a "unified, agentic Security Operations Center that combines AI-driven workflows with human expertise.
For those who are not familiar with Zscaler, a pioneer in Zero Trust and cloud-native security, has long been a category leader with its robust platform and deep enterprise adoption. But the company’s story is no longer just about early innovation—it’s about strategic expansion. As enterprises shift toward hybrid work, AI workloads, and zero trust architectures, Zscaler is positioning itself as a critical control plane for secure digital transformation.
Why do we talk about Zscaler
The reason I’d like to write about Zscaler is because there are only ten companies in the history of cybersecurity history that have over 1B revenue, in the past 15 years, the number is three and Zscaler is one of them. If Zscaler makes it to the top ten in history, it must have done something right. Now, let us drive into the company to see more details.
The Founder’s Journey
Jay Chaudhry was born in Panoh, a remote village tucked away in the hills of Himachal Pradesh, India. The village had no electricity, no running water—just grit, community, and a quiet determination. That same determination would define Jay’s life.
After earned his undergraduate degree in electronics engineering from IIT-BHU, one of India’s top technical institutes, he left for the United States to satisfy his ambitions, where he pursued not one, but three master’s degrees at the University of Cincinnati—in industrial engineering, computer engineering, and marketing—equipping himself with a rare combination of technical depth and business insight.
Jay spent his early career in the corporate world at IBM, Unisys, and NCR, gaining hands-on experience across engineering, sales, and leadership. But he wasn't destined to stay in the comfort of corporate halls. In 1996, alongside his wife, he launched SecureIT, a cybersecurity startup well ahead of its time. It was the first of several bold bets. Over the next decade, Jay would go on the roller coaster journey through the full life of the other three startups: CipherTrust, CoreHarbor, and AirDefense, selling them to industry giants like VeriSign, Secure Computing, and Motorola.
Founding Zscaler
The right person is waiting for the next big opportunity and it comes in 2007. In that year, the U.S. internet landscape was booming. The internet was experiencing explosive growth, bringing a surge in the majority of dominant .com companies we currently know and tons of shared resources. Alongside this growth came a wave of web-based threats: botnets, malicious content, and phishing attacks proliferated rapidly.
In this suddenly hostile and increasingly complex security environment, traditional on-prem security gateways used by distributed enterprises began to fall short. The emerging risks sharpened Jay’s conviction: the future of security wouldn’t be built on hardware boxes—it would live in the cloud. That conviction became Zscaler. As a successful entrepreneur Jay knows one tree does not make a forest so he quickly reconnected with Kailash—his classmate from IIT—at a conference in San Jose.
During the conference, Jay shared his vision of cloud-native security, and despite the technical challenges, Kailash quickly saw its potential. Kailash recalls:“After four months of development, discussion and lots of trial and error, it seemed that we had a viable solution.” Later on, as the Chief Architect, he led the foundational engineering to create a cloud-native Zero Trust platform.
Zscaler seized the opportunity by entering the Secure Web Gateway (SWG) market. The company offered core web protection capabilities, but differentiated itself by delivering them through a multi-tenant, distributed cloud architecture—distinct from the hardware-centric solutions of the time.
It promised better threat detection, lower total cost of ownership, easier management, and a flexible pay-as-you-go model—helping enterprises tackle web threats more efficiently and scalably. Jay believed that simple is more, he personally invested $50 million of his own money to fund its early growth, with just 10 engineers —half based in Bangalore, the other half working out of a borrowed office in the U.S. before Zscaler became a $32 billion company in 2012.
Early Competitors, Target Customers and GTM Strategy
The massive emerging market is never owned by just one player. By 2008, Blue Coat, Secure Computing acquired by McAfee, Websense, Trend Micro, and ScanSafe were also making aggressive moves. Zscaler had to compete against appliance-heavy giants with mature, boxed solutions. In order to survive, they moved smartly to solve its first burden: handling network traffic meant bearing direct infrastructure costs—a tough proposition for a startup without the backing of appliance-based revenue models.
The smart way is to find a good partnership which has network effects as the distributor. After the deep research, they found one: Service Providers (SPs)—the broadband network operators. Back then, service providers were facing serious challenges of their own. The broadband access market had become fiercely competitive, as cable MSOs and telecom carriers battled for dominance over residential and SMB customers.
To attract and retain users, SPs were forced to bundle multiple services—TV, wireless, voice, and internet—into a single offering. As a value-added service provider to secure users and traffic in the cloud, Zscaler integrated into this ecosystem and started to acquire the customer through the handle network delivery of SP distribution. However, most SP customers were small businesses and residential users, they weren’t the ideal long-term customer profile to sustain a high-growth enterprise SaaS model.
It is time that the company starts to build up its own enterprise sales team. Zscaler targeted customers who have tens of thousands of employees spread across global regions, requiring a unified cloud security control platform. These organizations are typically undergoing cloud migration, adopting SaaS applications (e.g., Office 365, Workday, Salesforce), or shifting to hybrid work models.
They are also replacing traditional VPNs and firewalls with identity-based Zero Trust access and granular access controls. Many customers have CISOs or CIOs championing Zero Trust and SASE adoption, they are also interested in having good ROI and IT Simplification during the vendor selection.
As such, in Zscaler GTM principle, it clearly claimed its target: “We don’t sell to network admins. We talk to business leaders about secure digital transformation.” Jay wasn’t just the founder—he was the first salesperson, relentlessly pitching to CIOs and CISOs about a new, cloud-native Zero Trust vision.
He brought to the table extensive domain knowledge and had set an early expectation: focus on solving customer problems, not on internal metrics or fiefdoms. It also scaled faster by leveraging channel partnerships including: VARs (Value-Added Resellers)—such as cybersecurity solution providers, ISVs (Independent Software Vendors) and began targeting sectors such as healthcare, government, finance, SMBs, education, and retail for sales.
Zscaler’s remarkable growth attracted funding right on schedule. They raised a $12 million Series A in 2008 led by Norwest Venture Partners, followed by a $38 million Series B in 2012 with participation from Lightspeed Venture Partners.
Product
Pure cloud-native architecture & Zero Trust
From 2012 to 2016, Zscaler’s evolution toward Zero Trust and global scale, including SSL decryption, ZPA launch, and POP expansion.
Imagine a modern office building where you need to scan your badge to enter—not just the front door, but every room you access. Your badge only works for areas you're approved to enter, and security checks your identity, role, and device each time. Even if someone steals a badge, they can’t get far—every move is logged and reverified. That’s Zero Trust: no implicit trust, continuous verification, and least-privilege access—everywhere, every time. From a technical standpoint, every access request must be continuously verified based on identity, device posture, location, and more, before granting limited, least-privilege access.
The concept was first formalized by John Kindervag, a Forrester Research analyst, in 2010. He challenged the idea that internal networks should be trusted by default. Zscaler is one of the pioneers and leading enablers of the Zero Trust model. It didn’t just adopt Zero Trust—it operationalized it at internet scale, helping thousands of companies move beyond legacy VPNs and perimeter firewalls to a modern, identity-based security model.
The unique architecture made this concept perfectly match Zscaler’s strategic focus. Zscaler built its platform from day one to be cloud-based and distributed, making it scalable, fast, and location-agnostic—key to supporting Zero Trust at global scale. The Zero Trust Exchange connects users only to specific applications, based on identity, posture, and context—exactly what Zero Trust calls for. In 2014, Zscaler added automatic SSL/TLS decryption & inline APT protection, bringing full visibility to encrypted traffic—a cornerstone of Zero Trust inspection.
Trying to move quickly on the Zero Trust product, in 2015, they secured a $110 million Series D, which included a $25 million extension led by Google Capital(now CapitalG).
In 2016, while most enterprises were still buying firewalls and expanding VPN capacity, Zscaler launched something radically different: Zscaler Private Access (ZPA)—a cloud-native, software-defined alternative to VPNs. At the time, it was a bold, even risky move. Zero Trust Network Access (ZTNA) wasn’t yet an industry term. But the Zscaler team saw the cracks in the perimeter-based security model long before they made headlines. They believed users shouldn’t be trusted just because they’re “on the network.” Access should be based on identity, device posture, and context—and scoped only to the apps they need.
It wasn’t what CIOs were asking for. But it was what they were going to need. It was met with skepticism. Yet, early adopters—especially in financial services and tech—saw the value: better security, smoother user experience, and no VPN headaches. No one knows at that time, after just a few years during the CV-19, remote work exploded, VPNs collapsed under pressure, and ZPA went from “nice to have” to mission-critical overnight. What once sounded futuristic became the new standard.
To me, this is more than product vision. It’s a reminder that real leadership isn’t about following demand—it’s about building ahead of the curve and having the courage to bet on the right future.
IPO, Leadership Team & M&A
The past momentum culminated in a successful IPO in 2018, offering approximately 12 million shares at $16 each, raising $192 million—and a total of $220.8 million including over-allotments. The IPO provided capital to scale Zero Trust cloud and expand R&D. The company has continuously invested in leadership as it scaled—from architect and engineering leaders like Kailash and Sinha, to business executives like Canessa and Welch who drove SaaS and scaling strategies. Today’s team reflects a mature enterprise: combining innovation (Phil Tee on AI), product leadership, global sales (Mike Rich), and operational excellence—all under Jay’s consistent vision.
After the IPO, through nine M&A and internal R&D from 2018-2024, Zscaler enhanced the core product lines into the Security Service Edge (SSE) and Zero Trust markets through:
*2018-2020: Foundational Platform Expansion (2018 TrustPath, 2019 Appsulate and 2020 Cloudneeti & Edgewise Networks)
*2021-2022: Deepening Zero Trust & Cloud Capabilities (2021 Trustdome & Smokescreen Technologies and 2022 ShiftRight)
*2023: Platform Integration (2023 Canonic Security and Launched the unified Zero Trust Exchange Platform at Zenith Live)
*2024- Now: AI Expansion and AI & Data Security Enhancements (2024 Avalor & Airgap Networks and 2025 Red Canary) .
Main Product lines
In addition to its core products—ZIA (internet access), ZPA (private app access), ZDX (digital experience monitoring), and AI-powered threat protection which feeds real-time context and policy, All traffic funnels through the Zero Trust Exchange control plane—Zscaler has expanded into cloud and workload security with ZCP (Zscaler for Cloud Protection).
ZCP secures cloud infrastructure through posture control, workload segmentation, and secure app-to-app communication. The platform also includes browser isolation, SD-WAN/branch integrations, deception and privileged access for OT, and risk-based policy engines. All services are unified under the Zero Trust Exchange, Zscaler’s global control plane that enforces identity- and context-aware security across users, apps, and workloads.
Platform Strategy
From the product lines and M&A distribution, we can see the strong Platform Strategy from Zscalar’s product lines and how they interact with each other. From Secure Access to Unified Zero Trust Control:
1. Cloud-Native by DesignZscaler was built entirely in the cloud—no hardware, no retrofits.
Zscaler’s platform stands out by completely eliminating the need for traditional firewalls and hardware appliances. Built as a cloud-native service from day one, it secures user, app, and device traffic through a global Zero Trust Exchange—without backhauling, patching, or deploying physical boxes. This architecture reduces cost and complexity while enabling faster, more secure access anywhere users work. Unlike legacy vendors tied to perimeter firewalls, Zscaler delivers security as a scalable, inline cloud service—designed for the modern, perimeter-less enterprise.
In order to support the smooth operation of platform products, Zscaler also operates 150+ globally distributed Points of Presence (POPs)—essentially cloud data centers that serve as inline security checkpoints for user and application traffic. Every time a user connects to the internet or a private application, their traffic is routed through the nearest POP, where Zscaler inspects it in real-time using Zero Trust policies. Because POPs are globally distributed and co-located with major cloud providers (AWS, Azure, etc.), users get fast and secure access to apps, regardless of location.
The strategy minimizes latency and maximizes resilience for global enterprises.
2. Unified Zero Trust ArchitectureZscaler connects users, workloads, and devices directly to apps—not networks—through its Zero Trust Exchange. This eliminates lateral movement, reduces attack surface, and enforces identity- and context-aware policies in real time.
3. Platform Core: ZIA + ZPA + ZDX + ZCP
ZIA: Secures internet access (SWG, CASB, DLP, Cloud Firewall)
ZPA: Zero Trust access to private apps
ZDX: Measures digital experience across user-to-app paths
ZCP: Protects cloud workloads, app-to-app traffic, and DevOps pipelines
4. AI-Driven Security and Policy AutomationWith acquisitions like Canonic, Avalor, and Red Canary, Zscaler is embedding AI across its platform—enhancing threat detection, risk scoring, posture visibility, and SOC automation.
5. Open Ecosystem IntegrationZscaler partners with Microsoft, CrowdStrike, Okta, AWS, ServiceNow, and others to create a flexible, API-driven ecosystem for identity, incident response, and governance.
6. Full-Spectrum SSE and BeyondAs a leader in Security Service Edge (SSE), Zscaler delivers an integrated solution that spans ZTNA, SWG, CASB, DLP, DEM, and now MDR/SOC—consolidating point solutions into one control plane.
The platform strategy is highly beneficial for Zscaler because it amplifies both business value and competitive advantage. It also drives growth, retention, and security outcomes—transforming it from a security vendor into a strategic control plane for enterprise connectivity and trust.
Competitors
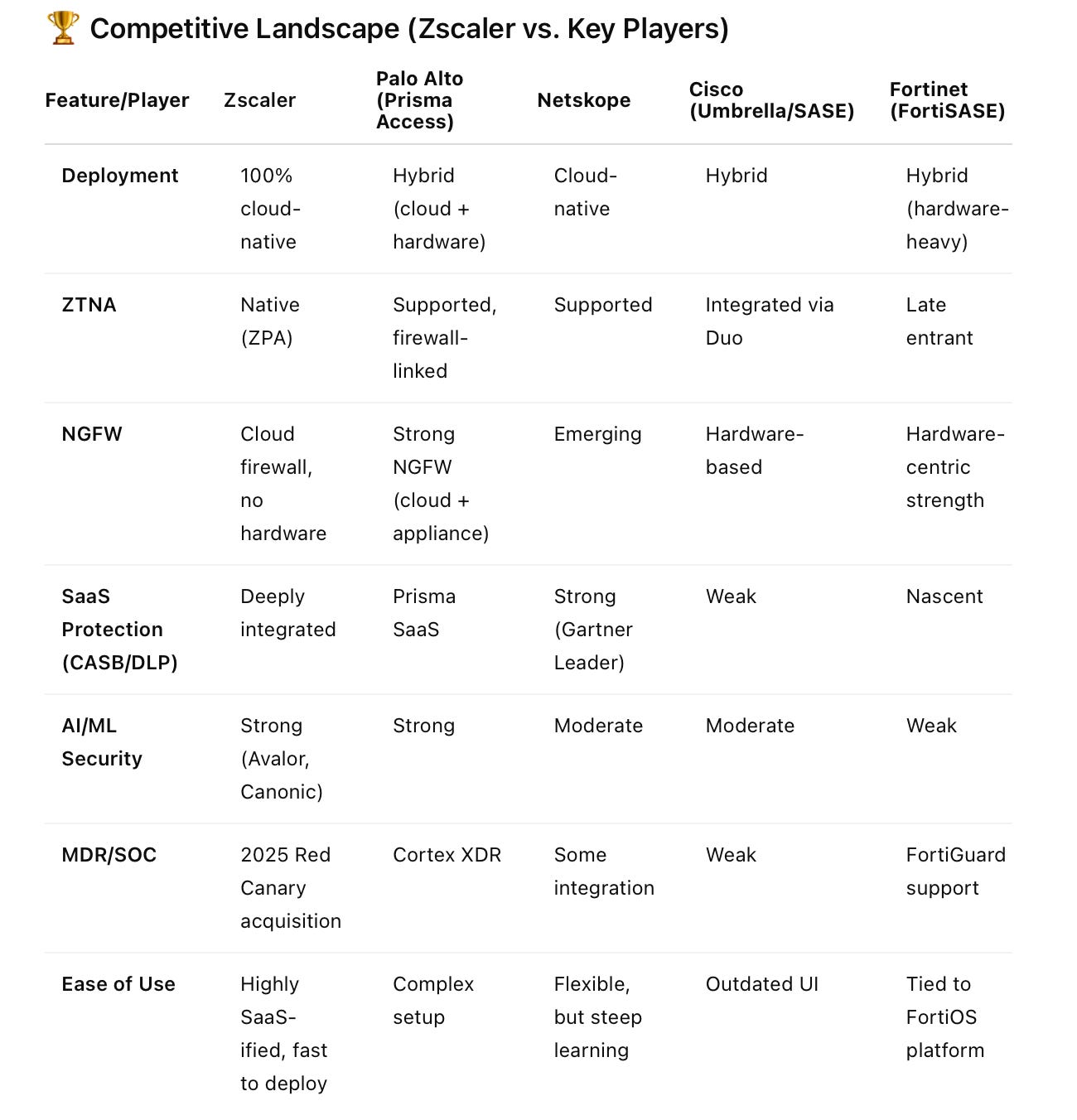
Again, all the profit business has more than one competitor. Zscaler’s competitors including Platform-Level Competitors (SSE + Zero Trust), Zero Trust & ZTNA Specialists, Cloud & Workload Security Rivals and Threat Detection & MDR / XDR. Here’s a concise competitive analysis of Zscaler compared to key players in the Security Service Edge (SSE) and Zero Trust markets:
Compared to other companies, Zscaler has its unique strengths:
Cloud-native architecture with flexible deployment and globally distributed acceleration nodes.
Industry-leading Zero Trust approach, with a closed-loop model via ZIA + ZPA + ZDX.
Rapidly advancing AI-driven data protection and threat detection capabilities.
Broad integrations with Microsoft, AWS, CrowdStrike, and an open ecosystem.
See more details of the competitive landscape below:
It also has some potential Challenges:
For large enterprises requiring full-stack observability, Zscaler’s log integration often depends on APIs or external SIEMs.
Some organizations still prefer hybrid or private cloud deployments, which may not align with Zscaler’s pure cloud model.
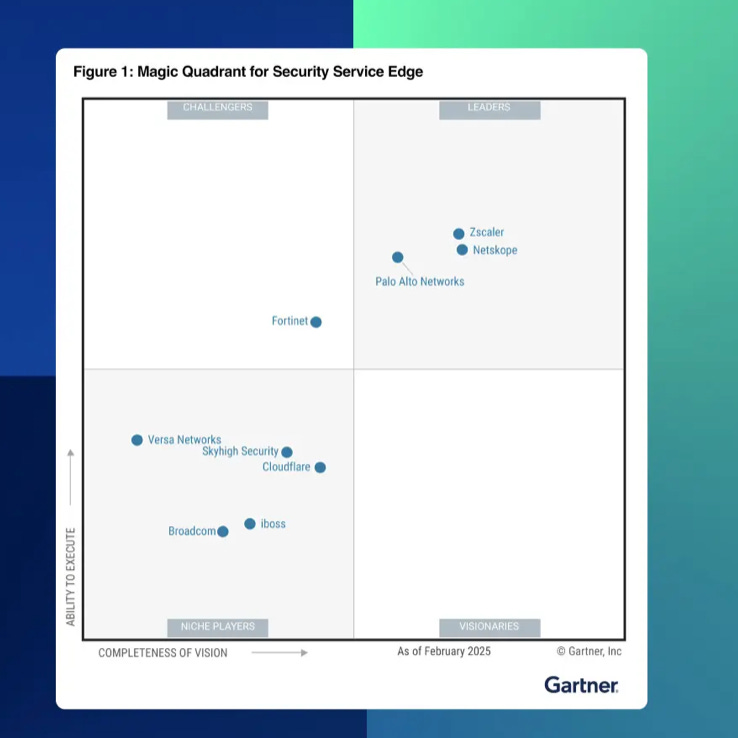
Although the competition is high, through the time, Zscaler helped define the Zero Trust implementation playbook for enterprises and is cited in many analyst reports(e.g., Gartner, Forrester) as a Zero Trust leader. Its architecture directly aligns with NIST SP 800-207 and supports federal Zero Trust mandates (e.g., EO 14028). In 2021, It was named a Leader in Gartner’s inaugural Security Service Edge (SSE) Magic Quadrant, which is the industry recognition that Zscaler’s platform delivers holistic Zero Trust at cloud scale.
Customer Success teams
Zscaler also has a great Customer Success teams to proactively help clients maximize product value after deployment with emphasizing customer-centric engagement, sales, and support.
Zscaler offers end-to-end lifecycle support, from initial implementation to daily operations, and tightly integrates this process with its channel partners. Their model embeds partners into every step of the customer journey—from early needs assessment to final deployment. These partners provide services and support, guiding customers through the transformation from traditional network architectures to a Zero Trust model.
This approach ensures that whenever customers face challenges with new product adoption, there is always someone available to assist—greatly enhancing the overall experience. Internally, Zscaler enforces cross-functional coordination for customer success, ensuring pre-sales, sales, delivery, and support teams work in sync with partners to quickly respond to client needs and feedback.
As a result, customers receive more than just a product—they benefit from a full solution and service experience, deepening their loyalty and trust in the Zscaler brand.
Current Financial Achievement
Doing the right things makes direct positive customer satisfactions and financial results - over 95% customer retention rate and average annual customer spend grows over 20%, reflecting expansion from ZIA to modules like ZPA, ZDX, and DLP. As a result, Zscaler's Q3 2025 financial results, released on May 29, 2025, showed a strong performance with revenue reaching $678 million, a 23% increase year-over-year. Annual Recurring Revenue (ARR) also grew to approximately $2.9 billion, representing a 23% year-over-year increase.
The Rule of 40 is a key SaaS valuation metric that combines revenue growth and profit margin to assess financial health. If the result is 40% or more, the company is considered to be in healthy financial shape for a high-growth SaaS business.
Based on the Zscaler’s financial numbers, in FY25Q3, its rule of 40 is 45%, signaling strong balance between growth and profitability. Despite a small GAAP net loss due to increased investment in sales, marketing, R&D, and integration efforts tied to recent initiatives—including acquisitions like Red Canary, its operational discipline and recurring revenue strength also place it among top-tier public cybersecurity companies.
What is the next for Zscaler
What is next? Data is the oil of the AI era, as the SaaS company with tons of data, Zscaler is positioning itself as the security foundation for the AI-first enterprise. As generative AI tools like Microsoft Copilot become mainstream, Zscaler is expanding its Data Security Everywhere strategy with prompt-level controls, AI-extended DLP, and full data protection across web, SaaS, email, endpoints, and GenAI apps. This is driving major enterprise wins, including multi-million-dollar deals with Fortune 50 and Fortune 100 companies. New capabilities like AI-Powered Segmentation and Digital Experience Network Intelligence further automate identity-based access and optimize network performance. As AI adoption accelerates, Zscaler’s platform is emerging as a critical layer for secure, compliant digital transformation.
Conclusion:
Zscaler began as a bold bet on a cloud-first future—at a time when enterprise security was still locked in hardware and perimeter firewalls. Through strategic acquisitions, cloud-native innovation, and deep CxO engagement, Zscaler evolved into a unified platform securing not just users—but workloads, data, and digital experience across cloud and hybrid environments. Now, with AI-powered threat protection, MDR expansion, and growing influence in DevSecOps, OT security and Data Security, let us see how Zscaler continues its journey to sharp the cybersecurity history.
Questions? My LinkedIn